Research
Fighting Deepfakes
Deepfake phenomenon has become very popular nowadays due to the possibility to create incredibly realistic images, videos and audio using deep learning tools, mainly based on ad-hoc Generative Adversarial Networks (GAN). The illicit use of these technologies (for example in the pornography industry) is increasing day by day, creating several problems in people's lives, spreading misinformation, political problems and many others. The goal of this research will be to create new sophisticated deepfake detection algorithms able to detect those forensic traces hidden in images and videos, a sort of fingerprint left in the synthetic multimedia data by the GAN engine generation process.
[Web Page] [Paper]
[Web Page] [Paper]
[Web Page] [Paper]
[Web Page] [Paper]
Forensic analysis of handwritten documents with GRAPHJ
 Luca Guarnera, Giovanni Maria Farinella, Antonino Furnari, Angelo Salici, Claudio Ciampini, Vito Matranga, Sebastiano Battiato (2018). Forensic analysis of handwritten documents with GRAPHJ. Journal of Electronic Imaging, 27(5), pp. 051230.
Luca Guarnera, Giovanni Maria Farinella, Antonino Furnari, Angelo Salici, Claudio Ciampini, Vito Matranga, Sebastiano Battiato (2018). Forensic analysis of handwritten documents with GRAPHJ. Journal of Electronic Imaging, 27(5), pp. 051230.
Web Page
Paper
We present GRAPHJ, a forensic tool for handwriting analysis. The proposed tool has been designed to implement the real forensic protocol adopted by the “Reparto Investigazioni Scientifiche” of Carabinieri, Italy. GRAPHJ allows the examiner to (1) automatically detect text lines and words in the document, (2) search for a specific character and detect its occurrences in the handwritten text, (3) measure different quantities related to the detected elements (e.g., heights and widths of characters), and (4) generate a report containing measurements, statistics, and the values of all parameters used during the analysis. The generation of the report helps to improve the repeatability of the whole process. The experiments performed on a set of handwritten documents show that GRAPHJ allows one to extract quantitative measures comparable to those acquired manually by an expert examiner. We also report a study on the use of the relative position of the superscript dot of the “i” characters as a parameter to infer the identity of the writer. The study has been performed using GRAPHJ and illustrates its value as a forensic tool..
A classification engine for image ballistics of social data
 Oliver Giudice, Antonino Paratore, Marco Moltisanti, Sebastiano Battiato (2017). A classification engine for image ballistics of social data. In International Conference on Image Analysis and Processing, pp. 625–636.
Oliver Giudice, Antonino Paratore, Marco Moltisanti, Sebastiano Battiato (2017). A classification engine for image ballistics of social data. In International Conference on Image Analysis and Processing, pp. 625–636.
Web Page
Paper
Image Forensics has already achieved great results for the source camera identification task on images. Standard approaches for data coming from Social Network Platforms cannot be applied due to different processes involved (e.g., scaling, compression, etc.). Over 1 billion images are shared each day on the Internet and obtaining information about their history from the moment they were acquired could be exploited for investigation purposes. In this paper, a classification engine for the reconstruction of the history of an image, is presented. Specifically, exploiting K-NN and decision trees classifiers and apriori knowledge acquired through image analysis, we propose an automatic approach that can understand which Social Network Platform has processed an image and the software application used to perform the image upload. The engine makes use of proper alterations introduced by each platform as features. Results, in terms of global accuracy on a dataset of 2720 images, confirm the effectiveness of the proposed strategy.
First quantization matrix estimation from double compressed JPEG images
Sebastiano Battiato, Oliver Giudice, Francesco Guarnera, Giovanni Puglisi (2021). First Quantization Estimation by a Robust Data Exploitation Strategy of DCT Coefficients. IEEE Access.
Paper
Sebastiano Battiato, Oliver Giudice, Francesco Guarnera, Giovanni Puglisi (2021). Estimating Previous Quantization Factorson Multiple JPEG Compressed Images. EURASIP Journal on Information Security.
Paper
Fausto Galvan, Giovanni Puglisi, Arcangelo Ranieri Bruna, Sebastiano Battiato (2014). First quantization matrix estimation from double compressed JPEG images. IEEE Transactions on Information Forensics and Security, 9(8), pp. 1299–1310.
Paper
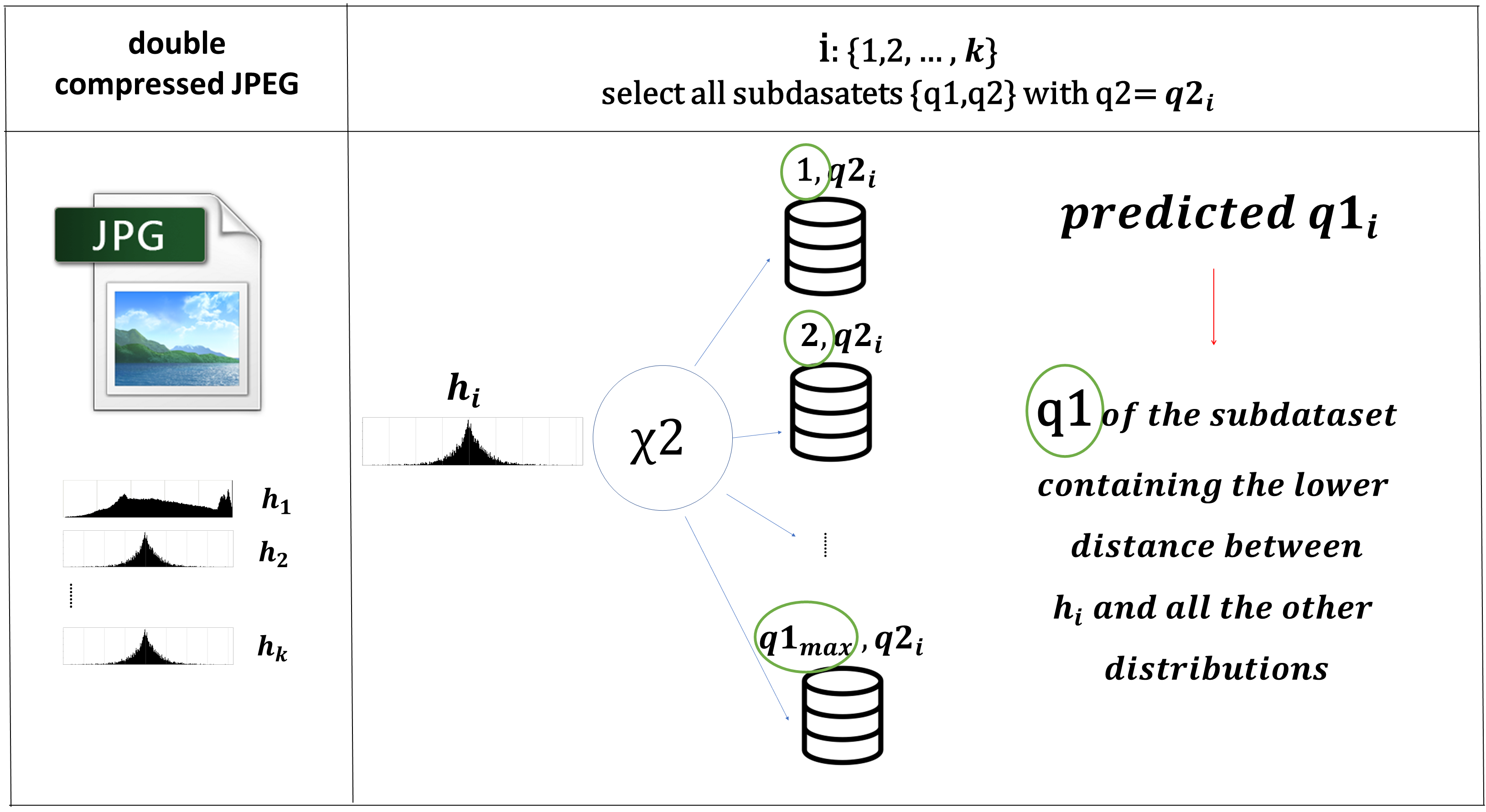
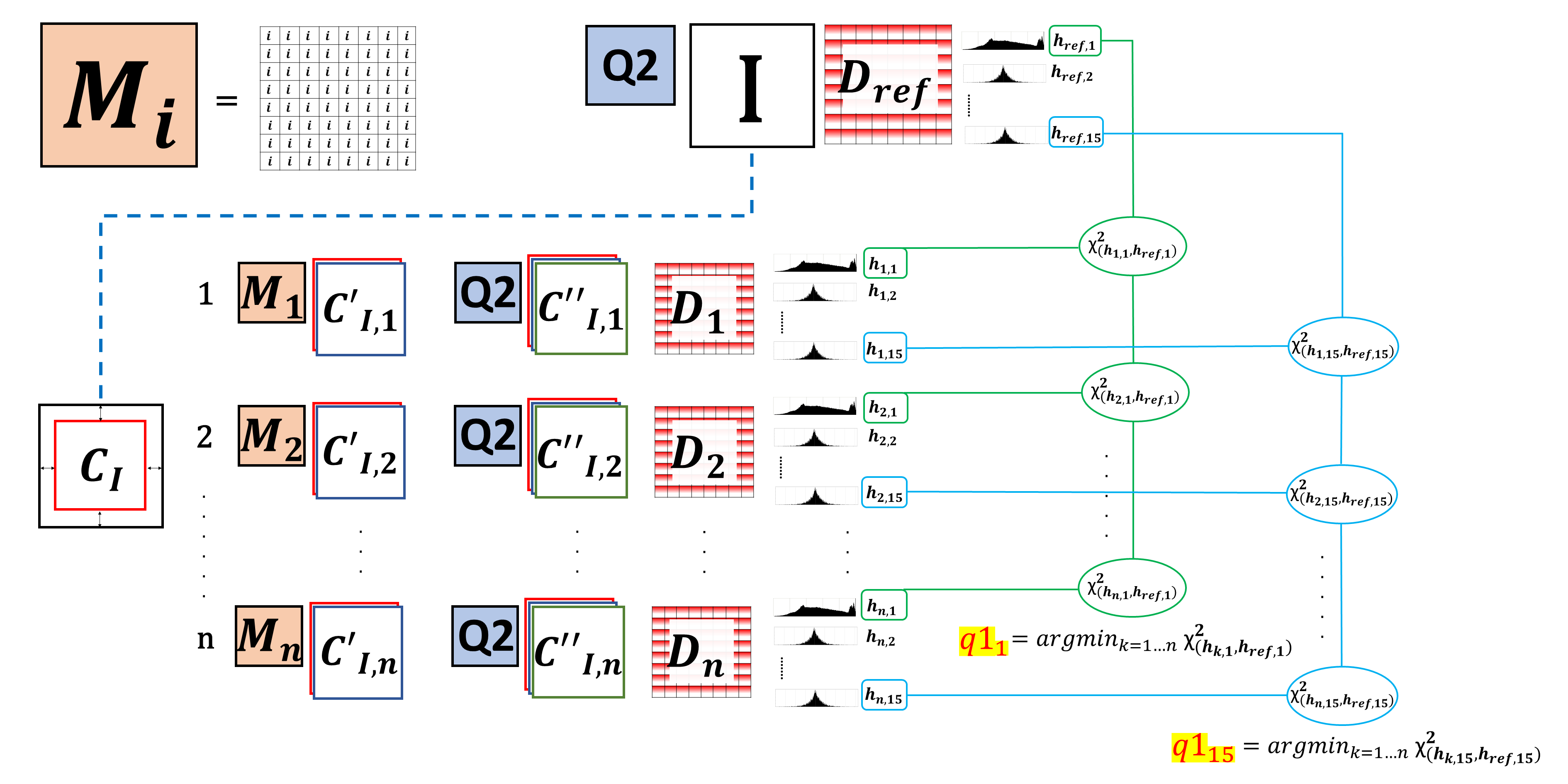
One of the most common problems in the image forensics field is the reconstruction of the history of an image or a video. The data related to the characteristics of the camera that carried out the shooting, together with the reconstruction of the (possible) further processing, allow us to have some useful hints about the originality of the visual document under analysis. For example, if an image has been subjected to more than one JPEG compression, we can state that the considered image is not the exact bitstream generated by the camera at the time of shooting. It is then useful to estimate the quantization steps of the first compression, which, in case of JPEG images edited and then saved again in the same format, are no more available in the embedded metadata. Galvan et al. (2014) copes with the case when the second quantization step is lower than the first one, exploiting the effects of successive quantizations followed by dequantizations. To improve the results of the estimation, a proper filtering strategy together with a function devoted to find the first quantization step, have been designed. Battiato et al. (2020) shows a technique based on extensive simulation, with the aim to infer the first quantization for a certain numbers of Discrete Cosine Transform (DCT) coefficients exploiting local image statistics without using any a-priori knowledge; it provides also a reliable confidence value for the estimation and good results also in the estimation of more previous quantization matrices. Battiato et al. (2021) proposed a method based on learning: a proper dataset of distributions was stored and then, given a new JPEG image a smart comparison technique permits to individuate the most similar distribution in the stored dataset, estimating the first quantization factor. The described papers represent the state of the art in the publication year w.r.t. the obtained results.
Aligning codebooks for near duplicate image detection
 Sebastiano Battiato, Giovanni Maria Farinella, Giovanni Puglisi, Daniele Ravì (2014). Aligning codebooks for near duplicate image detection. Multimedia Tools and Applications, 72(2), pp. 1483–1506.
Sebastiano Battiato, Giovanni Maria Farinella, Giovanni Puglisi, Daniele Ravì (2014). Aligning codebooks for near duplicate image detection. Multimedia Tools and Applications, 72(2), pp. 1483–1506.
Paper
The detection of near duplicate images in large databases, such as the ones of popular social networks, digital investigation archives, and surveillance systems, is an important task for a number of image forensics applications. In digital investigation, hashing techniques are commonly used to index large quantities of images for the detection of copies belonging to different archives. In the last few years, different image hashing techniques based on the Bags of Visual Features paradigm appeared in literature. Recently, this paradigm has been augmented by using multiple descriptors (e.g., Bags of Visual Phrases) in order to exploit the coherence between different feature spaces. In this paper we propose to further improve the Bags of Visual Phrases approach considering the coherence between feature spaces not only at the level of image representation, but also during the codebook generation phase. Also we introduce a novel image database specifically designed for the development and benchmarking of near duplicate image retrieval techniques. The dataset consists of more than 3300 images depicting more than 500 different scenes having at least 3 real near duplicates. The dataset has a huge variability in terms of geometric and photometric transformations between scenes and their corresponding near duplicates. Finally, we suggest a method to compress the proposed image representation for storage purposes. Experiments show the effectiveness of the proposed near duplicate retrieval technique, which outperforms the original Bags of Visual Phrases approach.
Forgery Detection and Value Identification of Euro Banknotes
 Arcangelo Bruna, Giovanni Maria Farinella, Giuseppe Claudio Guarnera, Sebastiano Battiato (2013). Forgery detection and value identification of Euro banknotes. Sensors, 13(2), pp. 2515–2529.
Arcangelo Bruna, Giovanni Maria Farinella, Giuseppe Claudio Guarnera, Sebastiano Battiato (2013). Forgery detection and value identification of Euro banknotes. Sensors, 13(2), pp. 2515–2529.
Web Page
Paper
This paper describes both hardware and software components to detect counterfeits of Euro banknotes. The proposed system is also able to recognize the banknote values. Differently than other state-of-the-art methods, the proposed approach makes use of banknote images acquired with a near infrared camera to perform recognition and authentication. This allows one to build a system that can effectively deal with real forgeries, which are usually not detectable with visible light. The hardware does not use any mechanical parts, so the overall system is low-cost. The proposed solution is reliable for ambient light and banknote positioning. Users should simply lean the banknote to be analyzed on a flat glass, and the system detects forgery, as well as recognizes the banknote value. The effectiveness of the proposed solution has been properly tested on a dataset composed by genuine and fake Euro banknotes provided by Italy’s central bank.
Robust image alignment for tampering detection
 Sebastiano Battiato, Giovanni Maria Farinella, Enrico Messina, Giovanni Puglisi (2012). Robust image alignment for tampering detection. IEEE Transactions on Information Forensics and Security, 7(4), pp. 1105–1117.
Sebastiano Battiato, Giovanni Maria Farinella, Enrico Messina, Giovanni Puglisi (2012). Robust image alignment for tampering detection. IEEE Transactions on Information Forensics and Security, 7(4), pp. 1105–1117.
Paper
The widespread use of classic and newest technologies available on Internet (e.g., emails, social networks, digital repositories) has induced a growing interest on systems able to protect the visual content against malicious manipulations that could be performed during their transmission. One of the main problems addressed in this context is the authentication of the image received in a communication. This task is usually performed by localizing the regions of the image which have been tampered. To this aim the aligned image should be first registered with the one at the sender by exploiting the information provided by a specific component of the forensic hash associated to the image. In this paper we propose a robust alignment method which makes use of an image hash component based on the Bag of Features paradigm. The proposed signature is attached to the image before transmission and then analyzed at destination to recover the geometric transformations which have been applied to the received image. The estimator is based on a voting procedure in the parameter space of the model used to recover the geometric transformation occurred into the manipulated image. The proposed image hash encodes the spatial distribution of the image features to deal with highly textured and contrasted tampering patterns. A block-wise tampering detection which exploits an histograms of oriented gradients representation is also proposed. A non-uniform quantization of the histogram of oriented gradient space is used to build the signature of each image block for tampering purposes. Experiments show that the proposed approach obtains good margin of performances with respect to state-of-the art methods.